17 KiB
| title | description |
|---|---|
| Traefik ForwardAuth Documentation | In Traefik Proxy, the HTTP ForwardAuth middleware delegates authentication to an external Service. Read the technical documentation. |
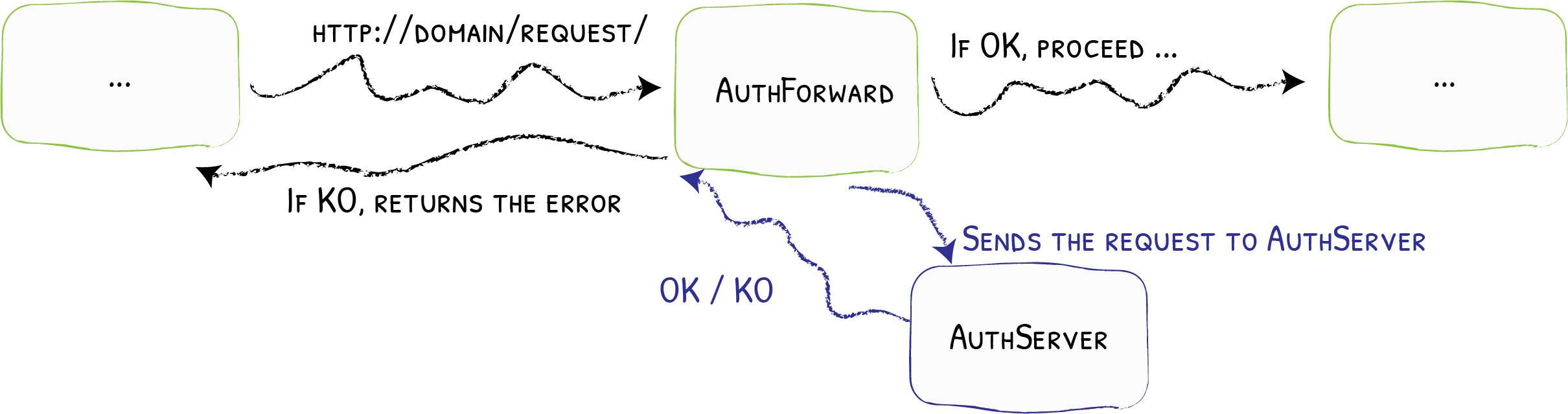
ForwardAuth
Using an External Service to Forward Authentication {: .subtitle }
The ForwardAuth middleware delegates authentication to an external service. If the service answers with a 2XX code, access is granted, and the original request is performed. Otherwise, the response from the authentication server is returned.
Configuration Examples
# Forward authentication to example.com
labels:
- "traefik.http.middlewares.test-auth.forwardauth.address=https://example.com/auth"
# Forward authentication to example.com
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-auth
spec:
forwardAuth:
address: https://example.com/auth
# Forward authentication to example.com
- "traefik.http.middlewares.test-auth.forwardauth.address=https://example.com/auth"
"labels": {
"traefik.http.middlewares.test-auth.forwardauth.address": "https://example.com/auth"
}
# Forward authentication to example.com
labels:
- "traefik.http.middlewares.test-auth.forwardauth.address=https://example.com/auth"
# Forward authentication to example.com
http:
middlewares:
test-auth:
forwardAuth:
address: "https://example.com/auth"
# Forward authentication to example.com
[http.middlewares]
[http.middlewares.test-auth.forwardAuth]
address = "https://example.com/auth"
Forward-Request Headers
The following request properties are provided to the forward-auth target endpoint as X-Forwarded- headers.
| Property | Forward-Request Header |
|---|---|
| HTTP Method | X-Forwarded-Method |
| Protocol | X-Forwarded-Proto |
| Host | X-Forwarded-Host |
| Request URI | X-Forwarded-Uri |
| Source IP-Address | X-Forwarded-For |
Configuration Options
address
The address option defines the authentication server address.
labels:
- "traefik.http.middlewares.test-auth.forwardauth.address=https://example.com/auth"
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-auth
spec:
forwardAuth:
address: https://example.com/auth
- "traefik.http.middlewares.test-auth.forwardauth.address=https://example.com/auth"
"labels": {
"traefik.http.middlewares.test-auth.forwardauth.address": "https://example.com/auth"
}
labels:
- "traefik.http.middlewares.test-auth.forwardauth.address=https://example.com/auth"
http:
middlewares:
test-auth:
forwardAuth:
address: "https://example.com/auth"
[http.middlewares]
[http.middlewares.test-auth.forwardAuth]
address = "https://example.com/auth"
trustForwardHeader
Set the trustForwardHeader option to true to trust all X-Forwarded-* headers.
labels:
- "traefik.http.middlewares.test-auth.forwardauth.trustForwardHeader=true"
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-auth
spec:
forwardAuth:
address: https://example.com/auth
trustForwardHeader: true
- "traefik.http.middlewares.test-auth.forwardauth.trustForwardHeader=true"
"labels": {
"traefik.http.middlewares.test-auth.forwardauth.trustForwardHeader": "true"
}
labels:
- "traefik.http.middlewares.test-auth.forwardauth.trustForwardHeader=true"
http:
middlewares:
test-auth:
forwardAuth:
address: "https://example.com/auth"
trustForwardHeader: true
[http.middlewares]
[http.middlewares.test-auth.forwardAuth]
address = "https://example.com/auth"
trustForwardHeader = true
authResponseHeaders
The authResponseHeaders option is the list of headers to copy from the authentication server response and set on
forwarded request, replacing any existing conflicting headers.
labels:
- "traefik.http.middlewares.test-auth.forwardauth.authResponseHeaders=X-Auth-User, X-Secret"
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-auth
spec:
forwardAuth:
address: https://example.com/auth
authResponseHeaders:
- X-Auth-User
- X-Secret
- "traefik.http.middlewares.test-auth.forwardauth.authResponseHeaders=X-Auth-User, X-Secret"
"labels": {
"traefik.http.middlewares.test-auth.forwardauth.authResponseHeaders": "X-Auth-User,X-Secret"
}
labels:
- "traefik.http.middlewares.test-auth.forwardauth.authResponseHeaders=X-Auth-User, X-Secret"
http:
middlewares:
test-auth:
forwardAuth:
address: "https://example.com/auth"
authResponseHeaders:
- "X-Auth-User"
- "X-Secret"
[http.middlewares]
[http.middlewares.test-auth.forwardAuth]
address = "https://example.com/auth"
authResponseHeaders = ["X-Auth-User", "X-Secret"]
authResponseHeadersRegex
The authResponseHeadersRegex option is the regex to match headers to copy from the authentication server response and
set on forwarded request, after stripping all headers that match the regex.
It allows partial matching of the regular expression against the header key.
The start of string (^) and end of string ($) anchors should be used to ensure a full match against the header key.
labels:
- "traefik.http.middlewares.test-auth.forwardauth.authResponseHeadersRegex=^X-"
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-auth
spec:
forwardAuth:
address: https://example.com/auth
authResponseHeadersRegex: ^X-
- "traefik.http.middlewares.test-auth.forwardauth.authResponseHeadersRegex=^X-"
"labels": {
"traefik.http.middlewares.test-auth.forwardauth.authResponseHeadersRegex": "^X-"
}
labels:
- "traefik.http.middlewares.test-auth.forwardauth.authResponseHeadersRegex=^X-"
http:
middlewares:
test-auth:
forwardAuth:
address: "https://example.com/auth"
authResponseHeadersRegex: "^X-"
[http.middlewares]
[http.middlewares.test-auth.forwardAuth]
address = "https://example.com/auth"
authResponseHeadersRegex = "^X-"
!!! tip
Regular expressions and replacements can be tested using online tools such as [Go Playground](https://play.golang.org/p/mWU9p-wk2ru) or the [Regex101](https://regex101.com/r/58sIgx/2).
When defining a regular expression within YAML, any escaped character needs to be escaped twice: `example\.com` needs to be written as `example\\.com`.
authRequestHeaders
The authRequestHeaders option is the list of the headers to copy from the request to the authentication server.
It allows filtering headers that should not be passed to the authentication server.
If not set or empty then all request headers are passed.
labels:
- "traefik.http.middlewares.test-auth.forwardauth.authRequestHeaders=Accept,X-CustomHeader"
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-auth
spec:
forwardAuth:
address: https://example.com/auth
authRequestHeaders:
- "Accept"
- "X-CustomHeader"
- "traefik.http.middlewares.test-auth.forwardauth.authRequestHeaders=Accept,X-CustomHeader"
"labels": {
"traefik.http.middlewares.test-auth.forwardauth.authRequestHeaders": "Accept,X-CustomHeader"
}
labels:
- "traefik.http.middlewares.test-auth.forwardauth.authRequestHeaders=Accept,X-CustomHeader"
http:
middlewares:
test-auth:
forwardAuth:
address: "https://example.com/auth"
authRequestHeaders:
- "Accept"
- "X-CustomHeader"
[http.middlewares]
[http.middlewares.test-auth.forwardAuth]
address = "https://example.com/auth"
authRequestHeaders = "Accept,X-CustomHeader"
tls
Optional
Defines the TLS configuration used for the secure connection to the authentication server.
ca
Optional
ca is the path to the certificate authority used for the secured connection to the authentication server,
it defaults to the system bundle.
labels:
- "traefik.http.middlewares.test-auth.forwardauth.tls.ca=path/to/local.crt"
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-auth
spec:
forwardAuth:
address: https://example.com/auth
tls:
caSecret: mycasercret
---
apiVersion: v1
kind: Secret
metadata:
name: mycasercret
namespace: default
data:
# Must contain a certificate under either a `tls.ca` or a `ca.crt` key.
tls.ca: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0=
- "traefik.http.middlewares.test-auth.forwardauth.tls.ca=path/to/local.crt"
"labels": {
"traefik.http.middlewares.test-auth.forwardauth.tls.ca": "path/to/local.crt"
}
labels:
- "traefik.http.middlewares.test-auth.forwardauth.tls.ca=path/to/local.crt"
http:
middlewares:
test-auth:
forwardAuth:
address: "https://example.com/auth"
tls:
ca: "path/to/local.crt"
[http.middlewares]
[http.middlewares.test-auth.forwardAuth]
address = "https://example.com/auth"
[http.middlewares.test-auth.forwardAuth.tls]
ca = "path/to/local.crt"
caOptional
Optional
The value of caOptional defines which policy should be used for the secure connection with TLS Client Authentication to the authentication server.
!!! warning ""
If `ca` is undefined, this option will be ignored, and no client certificate will be requested during the handshake. Any provided certificate will thus never be verified.
When this option is set to true, a client certificate is requested during the handshake but is not required. If a certificate is sent, it is required to be valid.
When this option is set to false, a client certificate is requested during the handshake, and at least one valid certificate should be sent by the client.
labels:
- "traefik.http.middlewares.test-auth.forwardauth.tls.caOptional=true"
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-auth
spec:
forwardAuth:
address: https://example.com/auth
tls:
caOptional: true
- "traefik.http.middlewares.test-auth.forwardauth.tls.caOptional=true"
"labels": {
"traefik.http.middlewares.test-auth.forwardauth.tls.caOptional": "true"
}
labels:
- "traefik.http.middlewares.test-auth.forwardauth.tls.caOptional=true"
http:
middlewares:
test-auth:
forwardAuth:
address: "https://example.com/auth"
tls:
caOptional: true
[http.middlewares]
[http.middlewares.test-auth.forwardAuth]
address = "https://example.com/auth"
[http.middlewares.test-auth.forwardAuth.tls]
caOptional = true
cert
Optional
cert is the path to the public certificate used for the secure connection to the authentication server.
When using this option, setting the key option is required.
labels:
- "traefik.http.middlewares.test-auth.forwardauth.tls.cert=path/to/foo.cert"
- "traefik.http.middlewares.test-auth.forwardauth.tls.key=path/to/foo.key"
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-auth
spec:
forwardAuth:
address: https://example.com/auth
tls:
certSecret: mytlscert
---
apiVersion: v1
kind: Secret
metadata:
name: mytlscert
namespace: default
data:
tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0=
tls.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCi0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0=
- "traefik.http.middlewares.test-auth.forwardauth.tls.cert=path/to/foo.cert"
- "traefik.http.middlewares.test-auth.forwardauth.tls.key=path/to/foo.key"
"labels": {
"traefik.http.middlewares.test-auth.forwardauth.tls.cert": "path/to/foo.cert",
"traefik.http.middlewares.test-auth.forwardauth.tls.key": "path/to/foo.key"
}
labels:
- "traefik.http.middlewares.test-auth.forwardauth.tls.cert=path/to/foo.cert"
- "traefik.http.middlewares.test-auth.forwardauth.tls.key=path/to/foo.key"
http:
middlewares:
test-auth:
forwardAuth:
address: "https://example.com/auth"
tls:
cert: "path/to/foo.cert"
key: "path/to/foo.key"
[http.middlewares]
[http.middlewares.test-auth.forwardAuth]
address = "https://example.com/auth"
[http.middlewares.test-auth.forwardAuth.tls]
cert = "path/to/foo.cert"
key = "path/to/foo.key"
!!! info
For security reasons, the field does not exist for Kubernetes IngressRoute, and one should use the `secret` field instead.
key
Optional
key is the path to the private key used for the secure connection to the authentication server.
When using this option, setting the cert option is required.
labels:
- "traefik.http.middlewares.test-auth.forwardauth.tls.cert=path/to/foo.cert"
- "traefik.http.middlewares.test-auth.forwardauth.tls.key=path/to/foo.key"
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-auth
spec:
forwardAuth:
address: https://example.com/auth
tls:
certSecret: mytlscert
---
apiVersion: v1
kind: Secret
metadata:
name: mytlscert
namespace: default
data:
tls.crt: LS0tLS1CRUdJTiBDRVJUSUZJQ0FURS0tLS0tCi0tLS0tRU5EIENFUlRJRklDQVRFLS0tLS0=
tls.key: LS0tLS1CRUdJTiBQUklWQVRFIEtFWS0tLS0tCi0tLS0tRU5EIFBSSVZBVEUgS0VZLS0tLS0=
- "traefik.http.middlewares.test-auth.forwardauth.tls.cert=path/to/foo.cert"
- "traefik.http.middlewares.test-auth.forwardauth.tls.key=path/to/foo.key"
"labels": {
"traefik.http.middlewares.test-auth.forwardauth.tls.cert": "path/to/foo.cert",
"traefik.http.middlewares.test-auth.forwardauth.tls.key": "path/to/foo.key"
}
labels:
- "traefik.http.middlewares.test-auth.forwardauth.tls.cert=path/to/foo.cert"
- "traefik.http.middlewares.test-auth.forwardauth.tls.key=path/to/foo.key"
http:
middlewares:
test-auth:
forwardAuth:
address: "https://example.com/auth"
tls:
cert: "path/to/foo.cert"
key: "path/to/foo.key"
[http.middlewares]
[http.middlewares.test-auth.forwardAuth]
address = "https://example.com/auth"
[http.middlewares.test-auth.forwardAuth.tls]
cert = "path/to/foo.cert"
key = "path/to/foo.key"
!!! info
For security reasons, the field does not exist for Kubernetes IngressRoute, and one should use the `secret` field instead.
insecureSkipVerify
Optional, Default=false
If insecureSkipVerify is true, the TLS connection to the authentication server accepts any certificate presented by the server regardless of the hostnames it covers.
labels:
- "traefik.http.middlewares.test-auth.forwardauth.tls.insecureSkipVerify=true"
apiVersion: traefik.containo.us/v1alpha1
kind: Middleware
metadata:
name: test-auth
spec:
forwardAuth:
address: https://example.com/auth
tls:
insecureSkipVerify: true
- "traefik.http.middlewares.test-auth.forwardauth.tls.InsecureSkipVerify=true"
"labels": {
"traefik.http.middlewares.test-auth.forwardauth.tls.insecureSkipVerify": "true"
}
labels:
- "traefik.http.middlewares.test-auth.forwardauth.tls.InsecureSkipVerify=true"
http:
middlewares:
test-auth:
forwardAuth:
address: "https://example.com/auth"
tls:
insecureSkipVerify: true
[http.middlewares]
[http.middlewares.test-auth.forwardAuth]
address = "https://example.com/auth"
[http.middlewares.test-auth.forwardAuth.tls]
insecureSkipVerify: true